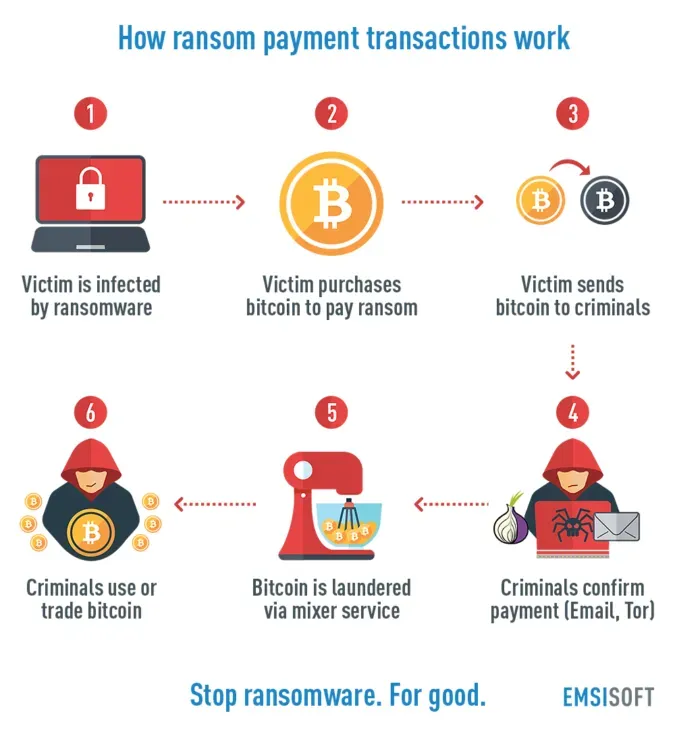
As the landscape of cybersecurity evolves, the new Ransomware Payment Reporting Rules, effective May 30, 2025, will bring substantial changes for businesses operating in Australia. Under these upcoming regulations, organizations will be mandated to report any ransom payments made during cyber incidents, fundamentally shifting how ransomware attacks are approached. This legislative move aims to enhance transparency and bolster national cybersecurity efforts, coinciding with broader strategies such as the establishment of a Cyber Incident Review Board. With the implementation of mandatory reporting cybersecurity practices, the government will gain critical insights into ransomware trends, thus enabling better resource allocation and support for affected businesses. For CEOs, understanding these rules is vital, as they must develop a comprehensive ransomware strategy that aligns with these evolving legal requirements and prepares them for rapid response during an attack.
With the looming introduction of Ransomware Payment Reporting Rules, businesses in Australia are facing a pivotal moment in their cyber incident management practices. Effective from May 30, 2025, these regulations will require companies to document and disclose any ransom payments made in response to cyberattacks. This shift not only highlights the need for proactive cybersecurity measures but also raises questions around the broader implications of such mandatory reporting. Every CEO must seriously evaluate their approach to ransomware, which now involves compliance alongside crisis management strategies to mitigate risks. Emphasizing transparency can serve as a potent tool in navigating the complexities of modern cybersecurity, ultimately reinforcing a company’s integrity in the face of adversity.
Understanding Australia’s New Ransomware Payment Reporting Rules
Effective May 30, 2025, Australia’s Ransomware Payment Reporting Rules will mandate businesses to notify the government about any ransom paid after a cyberattack within a strict 72-hour window. This regulatory move aims to enhance transparency in the face of rising ransomware threats and solidify the nation’s cybersecurity framework. By implementing such laws, authorities can better track ransom payments, understand the dynamics of ransomware attacks, and allocate resources more effectively to combat cybercrime.
Compliance with these new reporting rules is crucial for organizations, not just to avoid penalties but also to improve overall cyber incident management. Firms need to prepare their protocols and ensure that every aspect of their response strategy aligns with the legal requirements to report ransomware payments. This foresight can shield organizations against potential reputational and operational risks, placing them in a stronger position to handle future incidents.
The CEO’s Dilemma: To Pay or Not to Pay Ransom
A critical question facing many CEOs during a ransomware incident is whether to pay the demanded ransom. In the tumultuous aftermath of an attack, the allure of regaining access to essential data can pressure leaders into considering payment. However, this decision is fraught with uncertainty – paying does not guarantee file recovery and can inadvertently encourage further attacks, making it a precarious gamble. The CEO must weigh the immediate risks against the long-term implications for the organization.
Adopting a robust CEO ransomware strategy can significantly lessen the impact of these attacks. This strategy should involve comprehensive risk management, consistent employee training on cybersecurity best practices, and the establishment of a responsive incident management plan that can be activated swiftly. Being proactive could deter attackers and demonstrate to the cybercriminal community that the organization is prepared to resist extortion.
Responding Effectively During a Ransom Attack
When faced with a ransomware attack, the urgency of the situation cannot be overstated. Every moment spent scrambling for legal counsel or definitive reporting protocols can result in greater losses. Thus, businesses must have pre-rehearsed action plans that clearly outline steps for reporting ransomware incidents. This includes aligning the cybersecurity team with the legal department to ensure accurate and timely filing of necessary reports under the new rules.
Internal communication during a breach is equally critical. Organizations should develop crisis communication strategies that empower designated individuals to swiftly convey information to both internal stakeholders and external regulators. By ensuring that everyone involved knows their role beforehand, companies can act decisively, thereby enhancing their reputation and safeguarding their operations in the face of adversity.
The Importance of Transparency in Ransomware Reporting
Many leaders are concerned that reporting ransomware payments could expose them to public scrutiny or litigation. However, the opposite is often true. Transparency in reporting, especially as mandated by new government regulations, can bolster a company’s reputation. Demonstrating proactive compliance not only safeguards the organization against potential legal repercussions but also signals integrity to customers, partners, and investors.
By openly reporting ransomware incidents, businesses can contribute valuable data to the broader cybersecurity landscape, enhancing sector-wide vigilance against emerging threats. Firms that embrace mandated reporting can access government support initiatives designed to strengthen their defenses against future attacks, cementing their commitment to responsible cybersecurity practices.
Preparing for the Ransomware Reporting Deadline
With the deadline for compliance with the Ransomware Payment Reporting Rules fast approaching, organizations must prioritize preparation. Businesses should engage with legal and cybersecurity teams to dissect the new requirements, establishing clear accountability and procedures for incident reporting. This critical discussion helps ensure that everyone knows their responsibilities to avoid any last-minute scramble during an actual incident.
Moreover, reviewing your organization’s data backup processes is essential to facilitate recovery should a ransomware attack occur. Organizations must not only ensure backups exist, but also assess their operational effectiveness and speed. This comprehensive preparation requires an integrated effort from top management to ensure cybersecurity is viewed not merely as an operational concern but as an essential component of business continuity planning.
Frequently Asked Questions
What are the new Ransomware Payment Reporting Rules for businesses in Australia?
Starting May 30, 2025, under the Ransomware Payment Reporting Rules in Australia, businesses are required to report any ransom payments made in response to a cyberattack within 72 hours. This mandatory reporting is part of a national effort to improve transparency and cybersecurity, aimed at gathering data on the nature and scale of ransomware incidents.
Are there any exceptions to the Ransomware Payment Reporting Rules?
Yes, not every ransomware incident needs to be reported under the Ransomware Payment Reporting Rules. However, if a ransom payment is made, it must be reported within the specified timeframe. Businesses may still need to report the incident itself depending on their sector and existing cyber incident management obligations.
How should CEOs approach the decision to pay a ransom in light of the Ransomware Payment Reporting Rules?
CEOs face a tough dilemma when considering ransom payments. While paying may seem like the quickest way to restore operations, it is fraught with risks including potential data loss and ongoing vulnerabilities. The Ransomware Payment Reporting Rules add a layer of complexity, as any payment must be transparently reported, which could impact the company’s reputation and security posture.
What immediate actions should be taken during a ransomware attack according to the Ransomware Payment Reporting Rules?
During a ransomware attack, it’s critical to act swiftly and ensure that reporting protocols are understood and ready to be executed. Companies should have a pre-prepared plan detailing who is responsible for reporting ransomware payments and managing communications. Adhering to the Ransomware Payment Reporting Rules, accurate information must be reported promptly to help government agencies respond effectively.
What reputational risks do businesses face when reporting under the Ransomware Payment Reporting Rules?
While some CEOs worry that reporting ransomware payments may expose vulnerabilities, reporting under the Ransomware Payment Reporting Rules can actually enhance a company’s reputation. It shows commitment to transparency and responsibility, while failing to report can lead to serious consequences including penalties and loss of stakeholder trust in an environment increasingly threatened by cyberattacks.
What proactive steps can companies take now to align with the Ransomware Payment Reporting Rules before the deadline?
Before May 30, 2025, businesses should review and enhance their cybersecurity measures. This includes clarifying the roles and responsibilities for reporting under the Ransomware Payment Reporting Rules, improving backup and recovery systems, and ensuring that executive teams are actively involved in the cybersecurity strategy. Preparedness is key to effectively managing future ransomware incidents.
| Key Point | Details |
|---|---|
| Ransomware Payment Reporting Rules Effective Date | May 30, 2025 – Businesses must report ransomware payments within 72 hours. |
| Reporting Requirements | Only ransom payments must be reported, including amount, method, and recipient details. |
| Consequences of Paying Ransom | Paying ransom may not guarantee data recovery and risks encouraging future attacks. |
| Preparedness During Attacks | Establish clear processes and communication plans before an attack happens. |
| Transparency Benefits | Reporting incidents can protect reputation and provide access to governmental assistance. |
| Immediate Actions Required | Review reporting requirements and ensure leadership is engaged in cybersecurity. |
Summary
The Ransomware Payment Reporting Rules, effective from May 30, 2025, mandate that businesses must report ransom payments within a strict timeline. This shift not only enhances national cybersecurity efforts but also presents significant operational challenges for organizations facing ransomware threats. By understanding the intricacies of these rules and preparing accordingly, businesses can navigate the complexities of ransomware incidents while minimizing risks to their reputation and operational integrity.